Juniper Backdoor Only Possible Because Of NSA's Own 'Dual EC' Backdoor, Say Security Experts
Recently, Juniper Networks announced that it found “unauthorized code” (backdoor) in its NetScreen firewall operating system, ScreenOS. According to security experts, that “unauthorized code” may, in fact, have been “authorized” - by the NSA. Other hackers merely stumbled upon it and started using it as their own, with a few small changes to it.
The NSA backdoor in question is the controversial Dual EC algorithm for random number generation. It was standardized by the National Institute of Standards and Technology (NIST) in 2006 and then uncovered as a backdoor (PDF) by a Microsoft cryptographer (Neils Ferguson) in 2007. Many security experts have pointed out since then that the algorithm was orders of magnitude slower than other alternatives, so it never made sense for the NIST to standardize it in the first place - unless it was meant to be used as a backdoor.
Then, in 2013, thanks to some Snowden documents, it was revealed that the NSA paid RSA, an influential security company, $10 million to adopt Dual EC in its BSAFE security suite, and quickly thereafter NIST approved it as a standard as well.
Despite all of this, Juniper said that because it changed some parameters in it, Dual EC should be safe to use, and it will continue to use it in its systems:
“ScreenOS does make use of the Dual_EC_DRBG standard, but is designed to not use Dual_EC_DRBG as its primary random number generator. ScreenOS uses it in a way that should not be vulnerable to the possible issue that has been brought to light. Instead of using the NIST recommended curve points it uses self-generated basis points and then takes the output as an input to FIPS/ANSI X.9.31 PRNG, which is the random number generator used in ScreenOS cryptographic operations.”
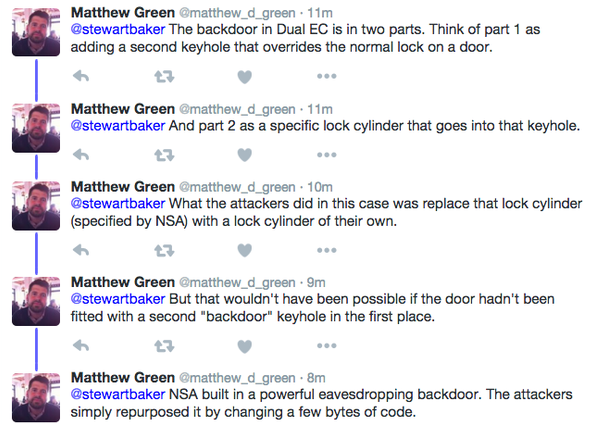
According to cryptography and network security professor Matthew Green, and others, this argument makes no sense, as the backdoor will continue to remain a backdoor, just with different parameters, as he explained on Twitter in more layman terms:
Even worse is that Juniper issued a "fix" that merely reverts the attackers' changed parameters to the original values Juniper was using for its firewalls. If those values get discovered by attackers, they could once again gain access to the system.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Matthew Green added in a later article on his Cryptography Engineering blog:
“To sum up, some hacker or group of hackers attacker noticed an existing backdoor in the Juniper software, which may have been intentional or unintentional -- you be the judge! They then piggybacked on top of it to build a backdoor of their own, something they were able to do because all of the hard work had already been done for them. The end result was a period in which someone -- maybe a foreign government -- was able to decrypt Juniper traffic in the U.S. and around the world.And all because Juniper had already paved the road.”
As Green also noted, this discussion is important to have because over the past few months, the U.S. government has tried to promote the argument that technology companies need to agree to a backdoor in their products, despite the almost unanimous cries from the security community that this would be devastating for digital security everywhere.
Some companies such as Apple, but also Google, have become the main targets of the U.S. government for their support of strong security and encryption. At the same time it’s been calling for security-weakening backdoors, the government has been arguing for increased “cybersecurity,” as a way to pass CISA, the surveillance bill in disguise, which has already been signed into law as the “Cybersecurity Act of 2015.”
“The problem with cryptographic backdoors is not that they're the only way that an attacker can break into our cryptographic systems. It's merely that they're one of the best. They take care of the hard work, the laying of plumbing and electrical wiring, so attackers can simply walk in and change the drapes,” Matthew Green added.
The whole Juniper backdoor situation should put to rest the “good guys” backdoor discussion, because as we can now see not just in theory, but also in practice, there’s no such thing as a backdoor that only the good guys (whoever they say they are) can use. A backdoor can and will be used by any attacker interested enough to look at someone’s backdoored code. As Green said, it also makes it much easier for them to exploit systems that otherwise would be more secure.
We have already asked Juniper Networks twice if there has been any cooperation between the company and the NSA regarding the use of the Dual EC algorithm, but so far it has refused to answer this question. We have also asked the company whether after all of these findings it is ready to completely eliminate the Dual EC code from its systems, because as many security experts note, reverting the parameters back to the company's original parameters is not a solution - eliminating Dual EC completely is. We'll update this article if a reply arrives.
Lucian Armasu is a Contributing Writer for Tom's Hardware. You can follow him at @lucian_armasu.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.
-
therealduckofdeath The NSA; breaking down democracy a little bit more every day.Reply
"Let's steal everyone's data"
"Let's leave the internet full of security holes" -
Effex Thank you for this informative article. Until now, I wasn't aware that Juniper was in league with he NSA to spy on people. That is unfortunate.Reply -
jeremy2020 Truly unfortunate. Best thing to do is replace Juniper hardware as soon as possible.Reply -
Darkk "We have already asked Juniper Networks twice if there has been any cooperation between the company and the NSA regarding the use of the Dual EC algorithm, but so far it has refused to answer this question. "Reply
This basically confirms the existence of backdoors for NSA to snoop on their customers.
I was actually looking into replacing our firewalls and networking equipment with Juniper. Now with this being brought into the light I will have to find another vendor.
Sorry Juniper. Should have stood your ground to protect your customers. This is going to cost you dearly.
-
KenZen2B Why is it that those that have purchased Juniper Networks products are not pursuing Juniper Networks for full refunds on ALL equipment ?Reply
Not pursuing refunds just lets Juniper Networks get away it. -
thor220 Good luck holding these guys accountable for anything. The budget bill that was just signed last week had many laws that had nothing to do with the budget attached. Included in there was a law that allows companies to freely share information with the government and be free of any and all liability for such an action. In otherwords, companies and the government may freely violate American citizen's rights (well, even more) and of course anyone who's data happens to pass over our servers.Reply
It's no wonder no one wants to do business with american IT firms. There's a 100% chance you are being watched, sentient or otherwise. -
KenZen2B Reply17177657 said:Good luck holding these guys accountable for anything. The budget bill that was just signed last week had many laws that had nothing to do with the budget attached. Included in there was a law that allows companies to freely share information with the government and be free of any and all liability for such an action. In otherwords, companies and the government may freely violate American citizen's rights (well, even more) and of course anyone who's data happens to pass over our servers.
It's no wonder no one wants to do business with american IT firms. There's a 100% chance you are being watched, sentient or otherwise.
Companies sharing data with government agencies is one thing, but putting in back doors that can be hacked is totally a different case. -
knight_of_baawa But...but....but....WE HAZ 2 B SAFE FRUM T3H MUZLIMZ! How can we be safe from them unless we let our respective governments spy on us all the time? How can we be safe unless we are constantly monitored???? We must be watched all the time OR T3H MUZLIMZ WILL WIN!!!Reply -
firefoxx04 First the government wants to hold companies responsible for data breaches.. and then they want back doors installed... which will cause more breaches.Reply
politicians are so stupid.