BitLocker reportedly auto-locks users' backup drives, causing loss of 3TB of valuable data — Windows automatic disk encryption can permanently lock your drives
Safety measures became an insurmountable barrier.
Microsoft introduced BitLocker storage encryption to Windows Vista in 2007. It was initially limited to only the Enterprise and Ultimate editions at the time, but since then, BitLocker has become an integral part of the operating system. Starting with Windows 11, BitLocker is turned on by default when you sign in with a Microsoft account in the OOBE. In theory, this is a novel practice — encrypting your storage without manual interception, but it can easily lead to unwanted problems.
That's what happened to an unfortunate user on Reddit, who was locked out of their data that vanished into the binary mazes of encryption, seemingly forever.
pcmasterrace from r/pcmasterrace/comments/1o9i0or/bitlocker_turned_itself_on_3tb_of_games_and
Feeling that their PC was lagging and not working to its fullest potential, u/Toast_Soup (let's call them Soup) decided to reset their PC and install a fresh copy of Windows. It's important to note at this point that Soup had six drives in its system; one of which is the boot drive, of course, and two massive data backups, each worth three terabytes, on the D: and E: disks. After the reinstall, when Soup booted into Windows, the latter two drives were essentially gone, encrypted by BitLocker, despite it never having been turned on in the first place.
See, Soup wasn't aware of the automatic encryption Microsoft enforces these days, so the thought to check first never even crossed their mind. Windows kept asking for a key that Soup never noted down (or even knew existed, for that matter), and without it, the drives are encrypted forever. There's no way to retrieve any data through recovery software — which Soup tried many of — because they can't break the BitLocker encryption. Its entire point is to act as a safeguard against bad actors, so as far as the drives are concerned, you're just trying to steal the data stored inside.
Lost and feeling hopeless, Soup performed another fresh reinstall, but to no avail, as the BitLocker screen appeared again, requesting a new key for the boot drive. Thankfully, Soup was aware of the game by now and knew to jot down that one, so they got inside Windows, but the two earlier drives were still locked. The comments on the post attempted to help our victim, suggesting that they check their Microsoft account settings. However, Soup clarified that only the key for the boot drive (C:) appears there, and nothing else.
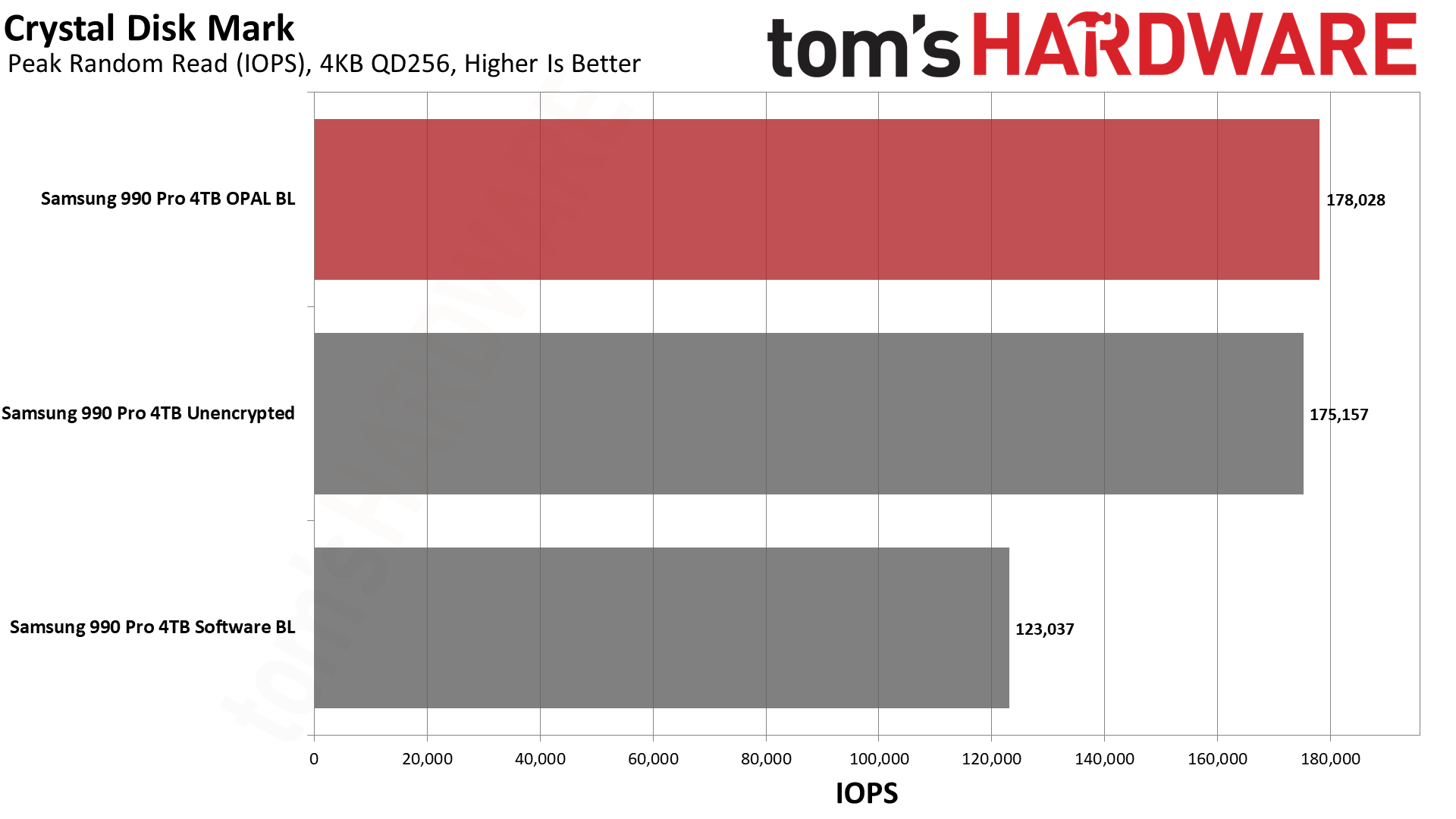
The best part is that this isn't even the extent of BitLocker's overreach. While nothing quite beats getting permanently (we hope not) locked out of your own data, a couple of years ago, we found out that BitLocker is surprisingly resource-intensive as well. In our testing, it slowed down random read/write speeds of the affected SSDs by up to 45% because it forces your CPU to encrypt and decrypt every single thing. This can genuinely slow down performance and make your PC feel sluggish, which is likely what Soup was experiencing in the first place. The signs were all there.
It's important to note that the software version of BitLocker that runs on your CPU differs from the hardware version (called "OPAL"). That runs even better than no drive encryption at all, but it's not the one that automatically turns itself on. Some comments from the Reddit thread suggest that even with a local account on Windows 11 Home, changes as small as tweaking the boot order can trigger BitLocker — if it isn't already enabled when you first set up your OS.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
BitLocker doesn't behave like this on Windows 10, or if you upgraded directly from that to 11. But, at this point, for Soup, there's nothing else that can be done beyond wiping those drives and starting over. We suggest staying vigilant in matters like these, where unwieldy corporations take away your autonomy to exercise what they feel is right. Check and turn off BitLocker following our original guide. Make sure to note down any important keys, and always keep backups of sensitive data that you can't afford to lose.

Follow Tom's Hardware on Google News, or add us as a preferred source, to get our latest news, analysis, & reviews in your feeds.

Hassam Nasir is a die-hard hardware enthusiast with years of experience as a tech editor and writer, focusing on detailed CPU comparisons and general hardware news. When he’s not working, you’ll find him bending tubes for his ever-evolving custom water-loop gaming rig or benchmarking the latest CPUs and GPUs just for fun.
-
Zaranthos A guy I work with was complaining about some encryption message he got on his computer that locked him out telling him he had to log into his Microsoft account and verify his key or something. I was like how did that pop up, were you on the internet doing something? He said, no he didn't even have internet, he only ever hooked it up to the internet once about a year ago when he set his new computer up, then took it home where he has no internet. My initial thought was be very careful, sounds like some scam to encrypt your data or get you to pay for something, but as he explained it more it sounded like BitLocker triggered for some unknown reason and required he verify his encryption key that was saved when he created his Microsoft account. Luckily he wrote his account info down so he can take his computer somewhere with internet and unlock Windows again.Reply
Forcing Microsoft accounts on people, especially people who don't even generally use the internet (yeah I know so rare these days, but it happens) is bad enough, but turning on encryption by default and tying it to a Microsoft account that many may never use again or even remember is even worse. He happened to use his computer for record keeping and never needed internet on it since he did online stuff on his phone. I advised him to turn off BitLocker once he got it up and running again as he had no need for it or a slower computer because of it. -
erazog This guy must have done something wrong or is leaving info out, bitlocker prompts the user to create recovery keys and by default stores them in your MS account or manually save to a text or file.Reply
Also even if a bitlocker drive goes faulty like turning the file system to raw it is possible to recover it if you have the key. -
ezst036 The reddit user seems to have found themselves in a unique situation. Hopefully Tom's Hardware does some fresh installs and testing to confirm what is and is not true.Reply
This is a really good point about the weakness whole system.Zaranthos said:A guy I work with was complaining about some encryption message he got on his computer that locked him out telling him he had to log into his Microsoft account and verify his key or something. I was like how did that pop up, were you on the internet doing something? He said, no he didn't even have internet, he only ever hooked it up to the internet once about a year ago when he set his new computer up, then took it home where he has no internet. My initial thought was be very careful, sounds like some scam to encrypt your data or get you to pay for something, but as he explained it more it sounded like BitLocker triggered for some unknown reason and required he verify his encryption key that was saved when he created his Microsoft account. Luckily he wrote his account info down so he can take his computer somewhere with internet and unlock Windows again.
Forcing Microsoft accounts on people, especially people who don't even generally use the internet (yeah I know so rare these days, but it happens) is bad enough, but turning on encryption by default and tying it to a Microsoft account that many may never use again or even remember is even worse. He happened to use his computer for record keeping and never needed internet on it since he did online stuff on his phone. I advised him to turn off BitLocker once he got it up and running again as he had no need for it or a slower computer because of it.
We have a lot of wizards of smart out there who think they are defeating the system by proclaiming that they created a Microsoft account "that one time" at install and ever since then they have created a local account and used only local accounts so HA HA HA on Microsoft because they won and Microsoft lost. Kind of foolish really.
The wizards of smart aren't factoring in that once you create the account and log in with it that the adware can now begin but this bitlocker adds a wrinkle to that.
Any security-conscious user will tell you:
Never write your passwords down.
So what is a wizard to do? Use the same password in multiple places? That is not a good security idea either. But is using multiple passwords better than writing it down because you know 3 years from now you'll still have not used it a second time?
What is a wizard of smart to do?
Overall I think Bitlocker is a good idea for protecting users data. It's the knife-to-your-neck online account that is the problem here. -
Alvar "Miles" Udell Bitlocker can be -incredibly- annoying on a desktop PC. The number of times I've had to look up and type in that recovery code because of a BIOS update or some faulty Windows update needs two hands, all for questionable benefit on a fixed system at low risk of being stolen for most people, unlike a laptop that travels.Reply
That being said it's an issue that takes less than five minutes to fix when it rarely happens, and this guy was a massive idiot for not only ensuring he knew how his system was running (if he didn't know Bitlocker was on may that laggy feeling was a cryptominer malware sapping his system), but also just backing things up to internal drives which is useless against fires, power surges, and other things that take out your system...Hopefully he learned his lesson and invested in a proper external backup drive. -
ceetee I ran into this last week when I turned on secure boot to install battlefield 6. I run 3 versions of windows on a multi boot setup... I could only get into 1 due to the boot manager asking for the keys... The one I got into I could get some keys from my ms account, but some weren't there. I was able to go to bit locker on the working install and save the keys to my ms account AND a USB drive... I left the drive plugged in and rebooted and the boot manager picked up the keys and everything is working again... I never knew this was a thing, now I'll make sure I have the keys backed up all the time....Reply -
tyns78 I just checked my laptop from summer 2023 on which I do not use a Microsoft account and both my drive volumes were 100% encrypted but had a Protection Status of Off. I'm decrypting them now and it's quite slow.Reply
edit: I formatted & reinstalled Win11 fresh upon receiving the laptop so it's not due to factory OEM install -
Bruce Benson Reply
Yup, unless you are a savant, you should not be using windows. Any good tech knows all the little tricks and gotchas and we get paid the big bucks for our knowledge.Alvar Miles Udell said:That being said it's an issue that takes less than five minutes to fix when it rarely happens, and this guy was a massive idiot ...Hopefully he learned his lesson and invested in a proper external backup drive.
Being appropriately secure and user friendly is not a winning strategy in this current age. Microsoft 's low quality was my business plan when I consulted for almost ten years. -
USAFRet Reply
I use a local standard account not as a "gotcha" to MS, but rather because the initial MS account is Admin.ezst036 said:We have a lot of wizards of smart out there who think they are defeating the system by proclaiming that they created a Microsoft account "that one time" at install and ever since then they have created a local account and used only local accounts so HA HA HA on Microsoft because they won and Microsoft lost. Kind of foolish really.
I'd rather not have the default account I'm using all the time have Admin rights. -
ukperson Reply
The OP's story doesn't sound right, as it only automatically turns on encryption for the OS drive. (If it's a clean install new pc with windows 11)erazog said:This guy must have done something wrong or is leaving info out. BitLocker prompts the user to create recovery keys and by default stores them in your MS account or manually saves them to a text file.
Also, even if a BitLocker drive goes faulty, like turning the file system to raw, it is possible to recover it if you have the key.
Other drives wouldn't have enabled bitlocker automatically it requires user input -
jlake3 Reply
The problem with Bitlocker is that there isn't really a better option than the knife-to-your-neck online account. I did some part-time IT work in the Windows 7 days and we had a few users using Truecrypt, and if you lost the keys for that you were totally SOL. That was something you had to actively seek out and install and came with several very scary warnings about irretrievable data loss, though, where as many users don't fully understand the sword of Damocles that Microsoft's default settings put over their PC. The Microsoft account at least gives some chance of recovery, but plenty of people have made it clear they don't want a Microsoft account and use a throwaway, and I absolutely know people who don't use theirs regularly and have forgotten their logins. Microsoft's dark patterns push you towards turning on Bitlocker without fully understanding the risk, then punishes you brutally if you aren't sufficiently committed to maintaining the account you didn't want to have.ezst036 said:Overall I think Bitlocker is a good idea for protecting users data. It's the knife-to-your-neck online account that is the problem here.
I'd have really rather preferred it remain opt-in rather than on-by-default. That would fix basically every issue I have with it.
And maybe Microsoft has better data, but ancedotally, data breach via physical device theft seems to be EXTREMELY rare relative to the number of people who installed trojans or gave up their credentials in a phishing attack.