Extortion Attempts Rise Alongside Memcached Amplification DDoS Attacks
GitHub, one of Akamai’s largest customers, was hit last week with a record-breaking 1.3 Terabit per second (Tb/s) distributed denial of service (DDoS) attack that used vulnerable memcached servers. Since then, Akamai has noticed that its customers have been receiving extortion messages delivered alongside the attack payloads.
DDoS Extortions
Extortion messages following DDoS attacks are not new. The extortion message senders could be the original group that previously launched an attack against a company and now wants to make money without spending any of its own on new attacks.
Alternatively, it could be scammers trying to take credit for the DDoS attack and make money by threatening other companies with new attacks. To show that they are “serious” the scammers may even demonstrate small attacks on the victim companies, and then warn that bigger attacks would come if the companies don’t pay up.
However, more often than not, these copycat attackers don’t have the capabilities to deliver those much larger attacks. Even so, some of those threatened may fall for it and pay up, which translates to easy money for the copycats.
Memcached Extortions
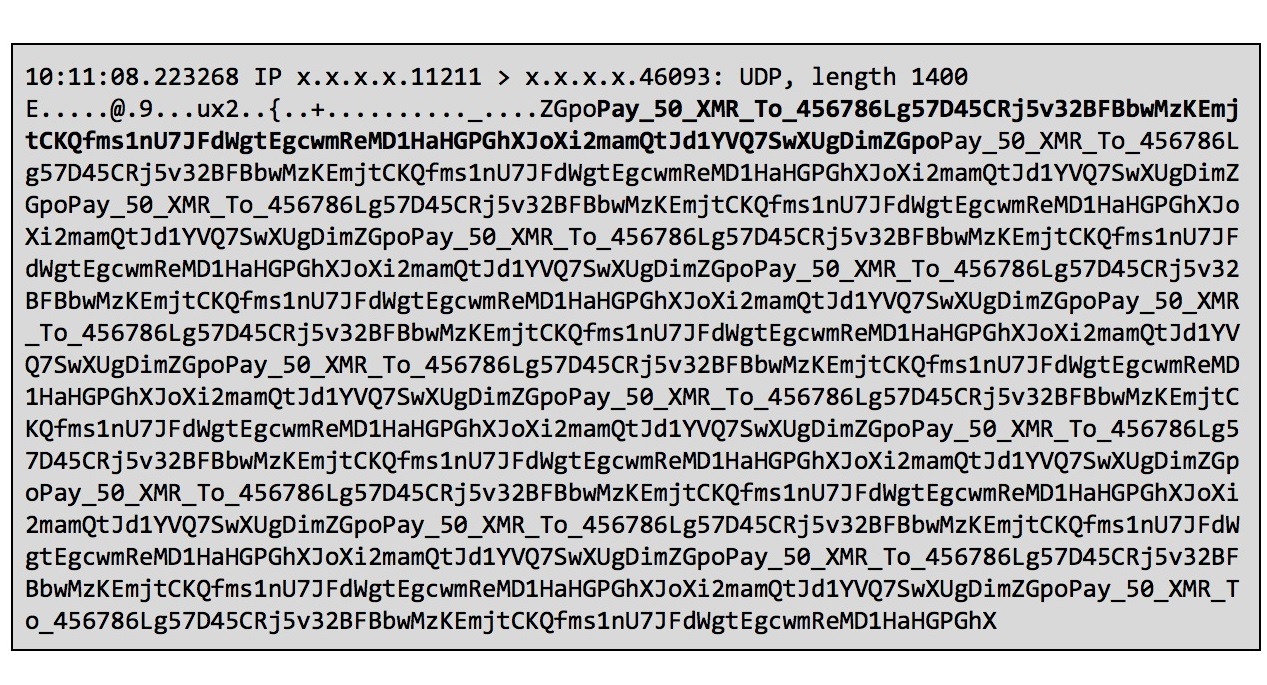
Following last week’s 1.3 Tb/s DDoS attack through vulnerable memcached servers, Akamai’s customers have started receiving extortion messages asking them for 50 Monero coins, which are currently valued at over $18,000.
Akamai said that multiple targets received the same message containing a Monero wallet address to which the victims could send their money. The extortion message packets were delivered along with the typically “junk-filled” attack payloads by exploiting the memcached servers.
Akamai warned its customers not to fall for these extortion tricks, because even if this represented a real threat, it doesn’t look like there’s any way for the attackers to even know which of their victims paid up. That means that even if some companies pay up, they may not necessarily escape the next attacks.
Stay On the Cutting Edge: Get the Tom's Hardware Newsletter
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
We also saw Akamai mitigate the record-breaking DDoS attack in less than 10 minutes last week, because it's now much better prepared to take on such large DDoS attacks. Therefore, unless the attackers have much larger attack capabilities ready to use, then paying the extortionists is completely unnecessary, in more ways than one.
