Signal Desktop Affected By Two Similar Remote Code Execution Bugs
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
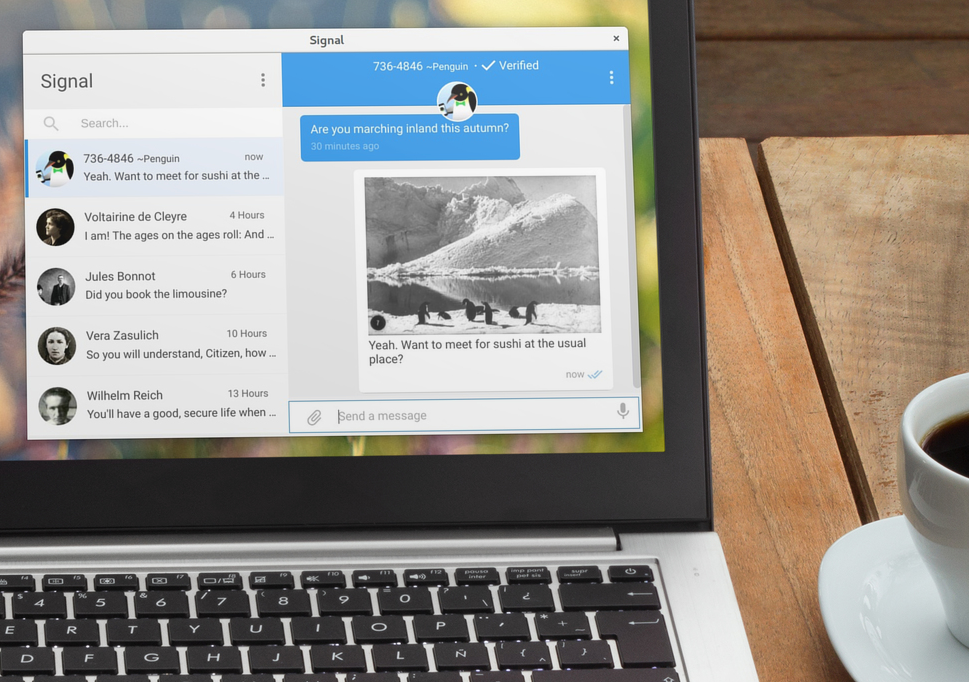
Researchers Iván Ariel Barrera Oro, Alfredo Ortega, and Juliano Rizzo found a remote code execution bug in the standalone desktop version of Signal, the open source private messenger used by whistleblower Edward Snowden, activists, journalists, U.S. electoral campaigns, and Senate staff. The bug could be exploited by a malicious contact who could inject “zero-click” malicious HTML code into the chat window and take over your machine.
Signal Remote Code Execution Vulnerability
According to Barrera, the vulnerability can be exploited when the Signal desktop application tries to parse a URL address. The Signal app fails to sanitize specific HTML tags that can be used to inject HTML code into chat windows.
More specifically, the "img" and "iframe" tags can be used to include remote or local resources, allowing an attacker to download or upload files, information, etc. The researcher also found the "script" tag to be injectable. On Windows, the JavaScript code is executed automatically, without any action required from the user. The attacker can trigger the vulnerability through a specially crafted message sent to the target.
Another Similar RCE In Signal Desktop
While testing the bug found by the other researchers, another web security researcher, Matthew Bryant, discovered a similar remote code execution bug. Bryant found that when he was sending a message with HTML markup such as <h1>Test</h1>, and then he was quoting that same message, the original markup would be evaluated as HTML. This attack would work even when the previous flaw, where the attacker only needed to send vanilla Signal messages that would be interpreted as HTML, was patched.
Both vulnerabilities were fixed by the Signal team within hours of being reported, so make sure you update immediately to the latest available version of Signal desktop. The vulnerabilities never affected the mobile versions of the app.
Bryant and his friends @aegarbutt and @LittleJoeTables also compiled a list of defense-in-depth recommendations for Signal desktop that they sent to the Signal developers to prevent us from seeing this sort of issue come up again in the future.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Lucian Armasu is a Contributing Writer for Tom's Hardware US. He covers software news and the issues surrounding privacy and security.