Thunderbolt Devices Could Infect Your PC, Thanks to Thunderclap Security Flaw

It's starting to seem like we should never plug anything into our computers. Shortly after it was revealed that USB cables can be used to remotely hack target systems, researchers discovered that Thunderbolt devices can be used to compromise a connected PC.
That discovery results from joint research between the Department of Computer Science and Technology at the University of Cambridge, Rice University and SRI International. They dubbed the vulnerability Thunderclap, for obvious reasons, and said they warned operating system makers about the findings before publicly disclosing them. According to Bleeping Computer, the paper was presented at the NDSS (network and distributed system security) 2019 conference this week.
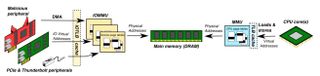
The Thunderclap vulnerability uses Thunderbolt over USB-C connections, aka Thunderbolt 3, to bypass the Input-Output Memory Management Units (IOMMUs) that defend against Direct Memory Access (DMA) attacks. This in turn "allows attackers to extract private data (sniffing cleartext VPN traffic) and hijack kernel control flow (launching a root shell) in seconds," according to the research report. PCs that use the Thunderbolt interface and have ports for connecting devices using PCIe and USB-C are vulnerable.
"An essential insight is that, while IOMMUs allow peripheral devices to be constrained, the DMA interface between device drivers and peripherals is a porous and complex attack surface that malicious actors can manipulate to influence software behavior and trigger vulnerabilities," the report says.
Someone could use a Thunderbolt device to compromise systems running Windows, macOS, Linux and FreeBSD. The paper noted Windows uses IOMMUs "only in limited cases." This method of attack can work over USB-C devices ranging from projectors to power adapters.
It would be hard to overstate the severity of these flaws. When it comes to their exploration of IOMMU security, the researchers said that "the results are catastrophic, revealing endemic vulnerability in the presence of a more sophisticated attacker despite explicit use of the IOMMU to limit I/O attacks."
Mitigation
Most people can probably sidestep the problem by not using suspicious cables and peripherals. Apple, Microsoft and Intel are said to have "issued security updates to partially address these concerns." Additionally, the researchers advised that people disable the Thunderbolt interface entirely for ultimate security. If you do so via firmware settings, you should still be able to use the port for its other functions.
Stay On the Cutting Edge: Get the Tom's Hardware Newsletter
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Want to comment on this story? Let us know what you think in the Tom's Hardware Forums.

Nathaniel Mott is a freelance news and features writer for Tom's Hardware US, covering breaking news, security, and the silliest aspects of the tech industry.
Intel roasts AMD and Nvidia in its latest product security report, claiming AMD has vulnerabilities with no fix planned, Nvidia has only high-severity security bugs [Updated]

Backdoor uncovered in China-made patient monitors — Contec CMS8000 raises questions about healthcare device security
