Protect Your Data With Encryption
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
You are now subscribed
Your newsletter sign-up was successful
Commencing Encryption For A Windows System
Here is what the encryption process looks like. You need to start by downloading TrueCrypt 6.1, and starting the encryption wizard from within the program.
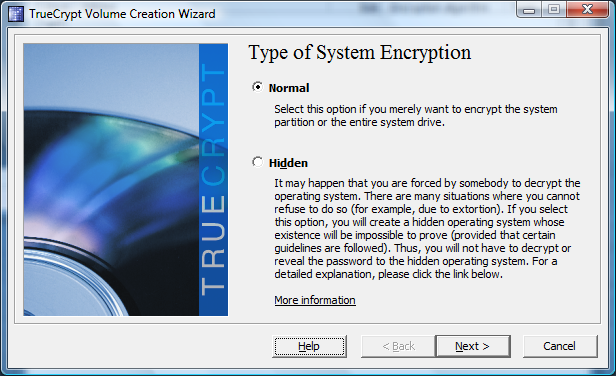
First of all you, have to select whether you only want to encrypt your system partition, or create a hidden system partition, which will be totally invisible. This latter option would be useful if someone forces you to decrypt a partition—you cannot be forced to decrypt something that isn’t there. Since this feature only makes sense if you create two system installations (one of which you will reveal in a worst case) it is only really applicable in a few extreme scenarios, so we will not deal with this in detail here (Ed.: It's worth noting here that previous versions of TrueCrypt have been compromised, eliminating the guarantee of plausible deniability. It's possible that the software on your machine could give away the existence of data on a hidden partition).
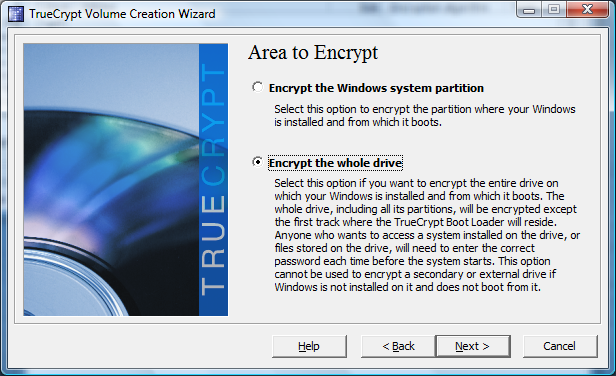
The next window asks you to select an encryption option. You can either only encrypt the Windows partition, which means that other partitions will be accessible, or you can encrypt the entire hard drive with all of its partitions. The second option is what we selected, as we want all data to be protected by the master password, which is entered as requested by the boot loader that starts the operating system.
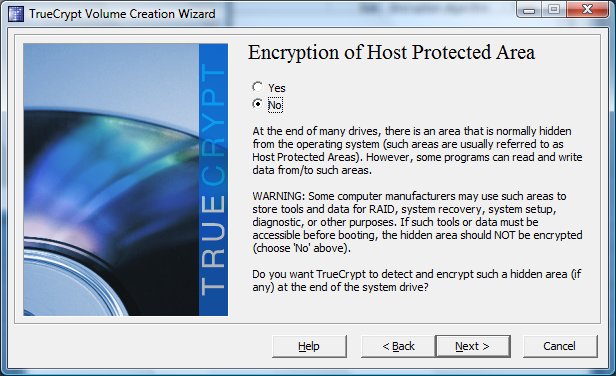
The third window prompts you to confirm or reject encryption for so called host protected areas. These can be partitions that are used by notebook vendors to store system recovery data.
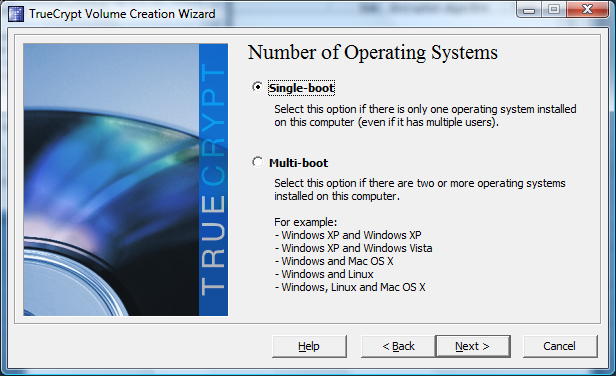
Window four allows selecting a single boot or a multi boot environment, as the TrueCrypt boot loader also acts as a boot manager. Select a multi-boot installation if you already run two different installations; check the screenshot for possible examples. We selected single boot, as we only used one Windows Vista partition.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
Current page: Commencing Encryption For A Windows System
Prev Page TrueCrypt 6.1 Features And Testing Considerations Next Page Encryption Algorithm, Performance, Rescue Disc