Hackers hope to democratize laser-based processor hacking — $500 RayV Lite relies on 3D printing, a laser pen, and a Raspberry Pi to bring costs down
Rival tools can easily cost 20x more.
Computer chips can be incredibly susceptible to bugs, as evidenced by the instability of 13th and 14th Gen Intel CPUs after excess voltage is applied to them. Security specialists also know that it’s possible for a well-targeted and well-timed laser light to cause glitches that expose vulnerabilities. One pair of hackers will soon release open-source plans to build one for around $500.
This light-based hacking technique takes advantage of the fact that the extreme miniaturization of transistors and other electrical components makes them vulnerable to the smallest variations in electrical charge. A precisely targeted and well-timed blast from a laser can knock the electrons within transistors out of place, causing glitches that can even bypass hardware security protocols.
State-of-the-art commercial tools used for this, such as the Riscure Laser Station, typically cost up to $150,000. Lower-budget, but still effective, options can be had for as little as $10,000.
However, two security researchers from NetSPI are about to unleash a set of open-source plans that use 3D printing, commonly available components, and a clever physics trick to build one for less than $500. One key to making this possible was the discovery by researchers at Royal Holloway University of London that lower-powered lasers fired at a chip for longer intervals could be as effective as a more powerful beam fired for a shorter time.
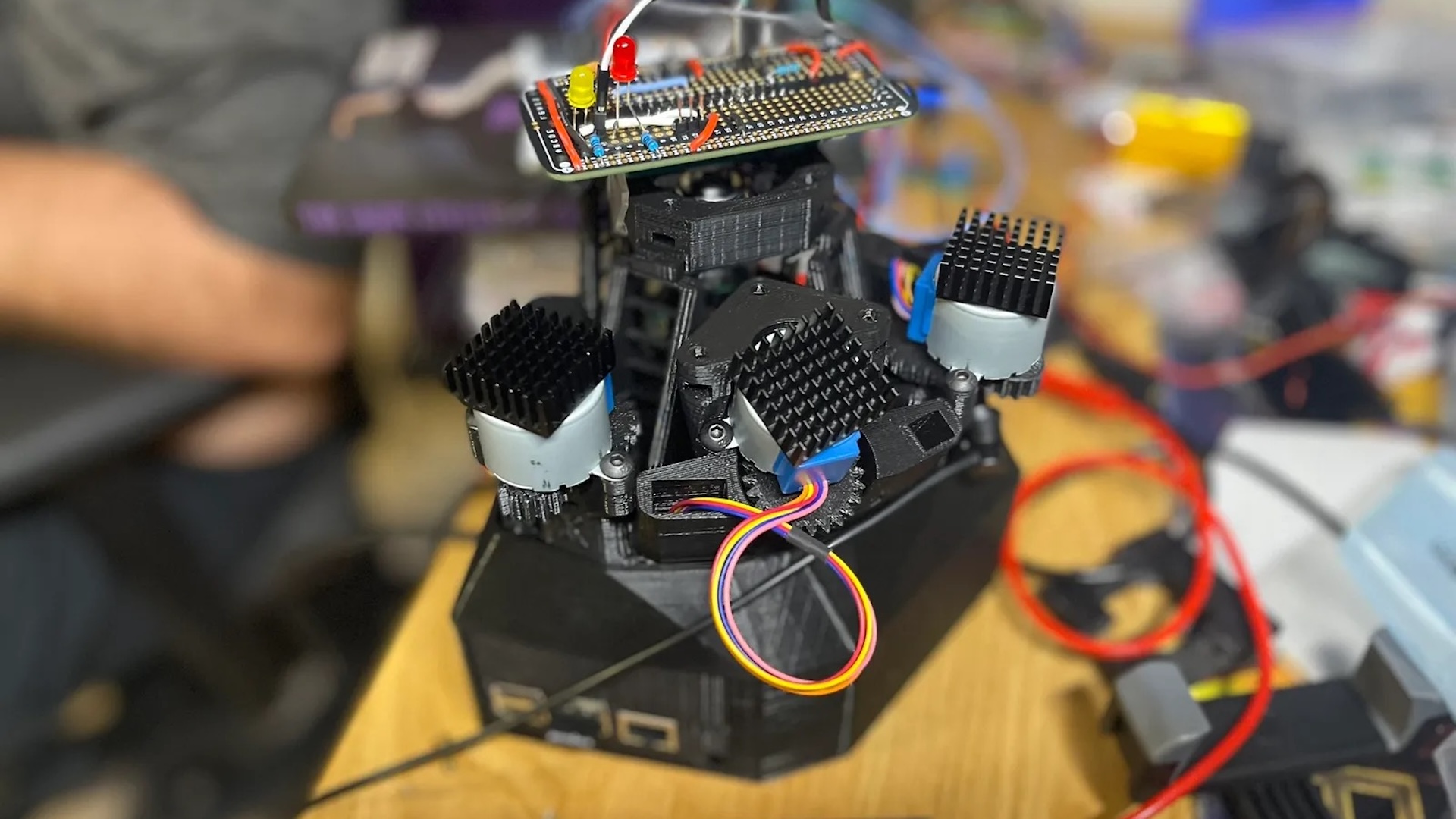
Sam Beaumont and Larry “Patch” Trowell, hackers at security firm NetSPI, have drawn up the design and component list for what they call the RayV Lite. This tool will allow anybody with the skillset to build a laser-based hacking tool right in their garage or basement for $500 or less. The duo plans to present the laser hacking device at the upcoming Black Hat cybersecurity conference in Las Vegas on August 8.
Beaumont and Trowell say their motivation for releasing the designs as open-source is to clarify to the world that laser-based exploitation techniques are more possible than many hardware designers believe them to be. They hope that by putting the tool in more hands, hardware manufacturers will be quicker to secure their products against this form of hacking.
“If we come to clients and say, ‘Your chip is vulnerable to laser fault injection,’ they tell us nobody's going to be able to do that because it's infeasible and it costs too much. We don't actually think that's true. So that got us started tinkering,” Beaumont says. “We're not discovering anything new, in the sense that other people have used lasers this way before. We're doing it at a lower cost, so that people can do this in their homes.”
Stay On the Cutting Edge: Get the Tom's Hardware Newsletter
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
The design the pair came up with uses components that are easy to acquire or make for yourself. The body of the tool is an adaptation of OpenFlexure, a 3D-printable microscope model. It uses the flexibility of PLA plastic to achieve very precise aiming of the laser beam. The most expensive components in the design, the lens used to focus the $20 laser beam and the FPGA chip for timing the pulse, cost close to $100 each. Even the computer used to run the show is an inexpensive Raspberry Pi they bought for less than $70.
The first of two versions of the RayV Lite will focus on laser fault injection (LFI). This technique uses a brief blast of light to interfere with the charges of a processor’s transistors, which could flip them from a 0 value to a 1 value or vice versa. Using LFI, Beaumont and Trowell have been able to pull off things like bypassing the security check in an automotive chip’s firmware or bypassing the PIN verification for a cryptocurrency hardware wallet.
The second version of the tool will be able to perform laser logic state imaging. This allows snooping on what’s happening inside a chip as it operates, potentially pulling out hints about the data and code it’s handling. Since this data could include sensitive secrets, LSI is another dangerous form of hacking that Beaumont and Trowell hope to raise awareness of.
Beaumont says that highly sensitive devices, like those used in industrial control systems, automobiles, and medical devices, will continue to be vulnerable to laser hacking techniques until manufacturers realize the reality of the threat. Organizations still believe the technology to conduct these attacks is arcane, expensive, and out of reach. Beaumont hopes that the work she and Trowell are presenting will change that.

Jeff Butts has been covering tech news for more than a decade, and his IT experience predates the internet. Yes, he remembers when 9600 baud was “fast.” He especially enjoys covering DIY and Maker topics, along with anything on the bleeding edge of technology.
-
fritzo New jailbreak era?Reply
I can see a future where systematic jailbreaks will once more be a game changer or hassle depending on who is property owner.
Root@linux without blobs should be a future we all want. The reason is easy.
Transparency makes trust!