USB-C cable CT scan reveals sinister active electronics — O.MG pen testing cable contains a hidden antenna and another die embedded in the microcontroller
A small package with a huge malicious potential.
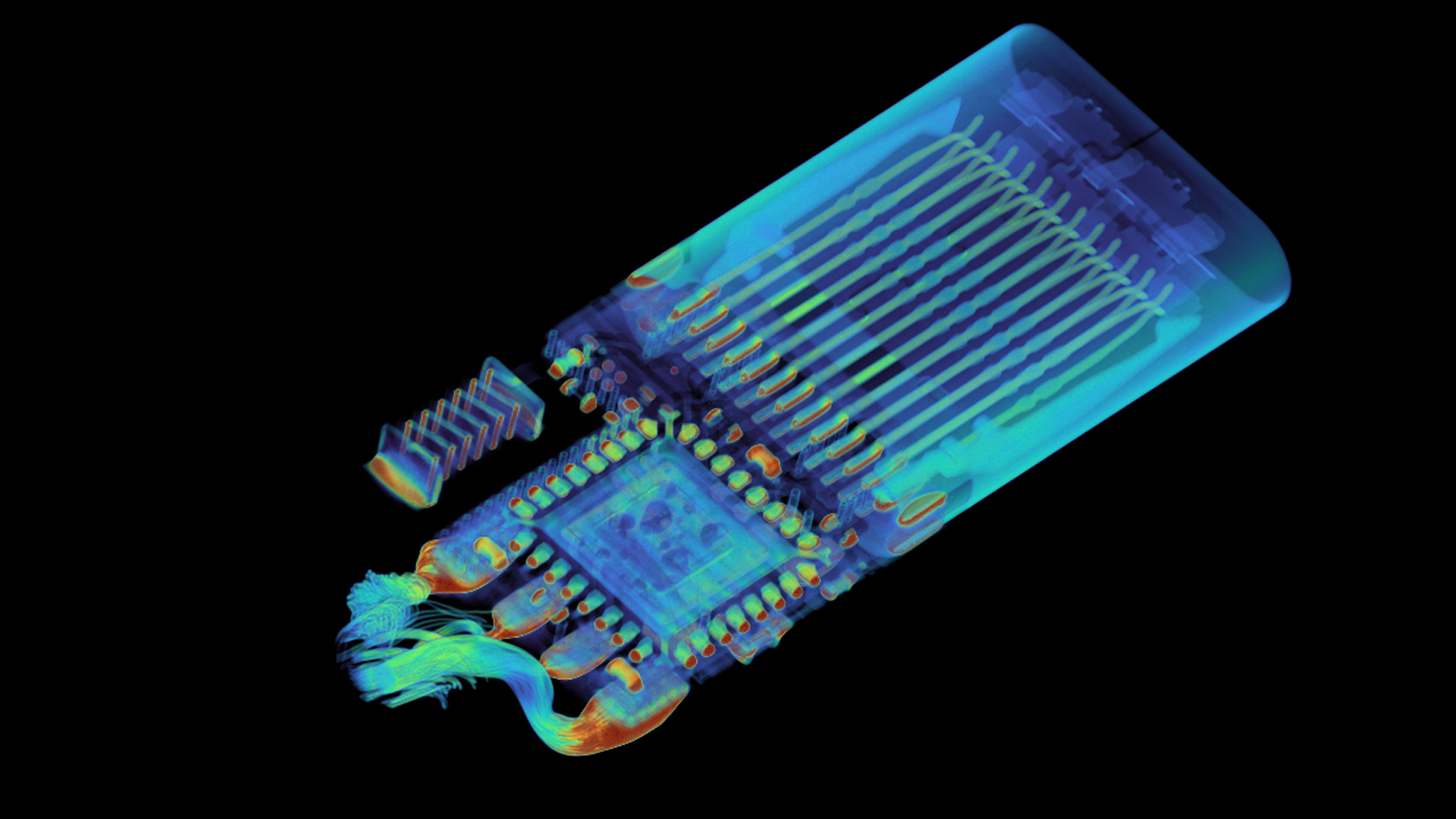
Industrial CT scanner manufacturer Lumafield imaged an O.MG USB-C cable, and found sophisticated electronic components secreted within the connector.
Lumafield product lead Jon Bruner shared on X (formerly Twitter) a CT scan that revealed the interior of the O.MG cable, showing advanced electronics and an antenna — a much more complicated design than the Amazon Basic USB-C cable that Lumafield scanned for comparison. Security researcher Mike Grover created this penetration-testing cable for fellow security researchers and hobbyists, red teamers, and for awareness training, especially for highly vulnerable or targeted individuals.
Aside from the microcontroller and antenna, Lumafield’s in-depth 3D CT scan revealed a second set of wires connecting a secondary die hidden under the primary microcontroller. This detail is difficult to spot in the scan, requiring some visualization parameter adjustments and a keen eye.
When the cable was passed through an ordinary 2D X-ray, this secondary die was practically invisible, letting it easily pass a cursory inspection. That means devices like this could conceivably pass through standard detection mechanisms.
The O.MG Elite USB-C cable has several features that could let anyone take over any device plugged into it. Some of its features include keystroke injection, mouse injection, geo-fencing, keylogging, and more.
Inside the ordinary-looking OMG connector we can immediately spot an antenna and a microprocessor. While high-end Thunderbolt connectors have some ICs, you won’t find an antenna like this in any normal USB connector. pic.twitter.com/EpLb8c2P6lDecember 4, 2024
Lumafield said that it did this scan after publishing an internal view of Apple’s Thunderbolt 4 (USB-C) Pro Cable, which revealed a lot of sophisticated electronics inside. Many wondered that if the tech giant could put such a lot of active components inside, maybe someone could put malicious hardware in something as mundane as a USB-C cable. So Lumafield decided to scan the O.MG cable to see how it hides its active electronics in such a tiny package.
The company's scan shows how a supply-chain attack can go undetected: With electronics as simple as charging cables getting more and more complicated every year, anyone, from run-of-the-mill hackers to state-sponsored attackers, could get into the manufacturing process of a device and insert systems that will compromise the final product, or worse.
Get Tom's Hardware's best news and in-depth reviews, straight to your inbox.
2D X-ray images can detect major deviations from an expected design, like the presence of an antenna and an IC, but it’s easy to slip other features past a simple 2D X-ray scan… pic.twitter.com/CwomA5ksvBDecember 4, 2024
One glaring example is the recent news of exploding pagers in Lebanon, where someone was able to insert powerful explosives into devices Hezbollah's leaders used for communication. The pagers changed hands several times — from Taiwan to Hungary — and no one could explain how they were compromised.
The good news is that these cables are expensive, with prices starting at $119.99 for the most basic version. So, you don’t have to be worried about someone spreading this malicious hardware to provide widespread chaos among the public at large.
Nevertheless, it’s better to be safe than sorry, so Bruner recommends that you purchase reputable charging cables sold by trusted stores and avoid public USB ports to charge your devices. If you really need power on-the-go, stick with the best USB-C laptop chargers to avoid getting your devices compromised.

Jowi Morales is a tech enthusiast with years of experience working in the industry. He’s been writing with several tech publications since 2021, where he’s been interested in tech hardware and consumer electronics.
-
Dr3ams When I worked as a network admin for Deutsche Telekom and Lufthansa this was a main concern for the American military, which used these companies' services in Germany. On bases the U.S. military would only allow telecommunications hardware built 100% in Germany. No boards with chips that might be made in China. Also, all Deutsche Telekom technicians servicing DSL or fiberglass systems on base had to be vetted.Reply -
JamesJones44 Did I miss read that the cable in question costs $119? If that's true, could this be a feature of the cable at that price vs malicious act?Reply -
bit_user Reply
I think the point of the article is rather subtle. This cable is clearly designed and advertised to be an attack vector (the article mentions features like "keystroke injection, mouse injection, geo-fencing, keylogging, and more"). However, they also give the example of Apple's cable having a microchip and I think their point is that a second chip can be concealed underneath a first.Co BIY said:But this was a one-off cable built by a security researcher and nothing in the article even mentions it being functional ?
IMO, this shows a big problem with relying on USB for power & charging. There should be "USB condoms" that disable all features besides power delivery, in case you need to take a charge from an unfamiliar USB source or cable. They should work just like a surge protector (which is also something they could do), by being a little hardware dongle that you connect through. -
Co BIY ReplyJamesJones44 said:Did I miss read that the cable in question costs $119? If that's true, could this be a feature of the cable at that price vs malicious act?
Yes the CT company bought the cable, which is designed and sold for hackers, to demonstrate their tech. -
Co BIY Replybit_user said:I think the point of the article is rather subtle. This cable is clearly designed and advertised to be an attack vector (the article mentions features like "keystroke injection, mouse injection, geo-fencing, keylogging, and more"). However, they also give the example of Apple's cable having a microchip and I think their point is that a second chip can be concealed underneath a first.
IMO, this shows a big problem with relying on USB for power & charging. There should be "USB condoms" that disable all features besides power delivery, in case you need to take a charge from an unfamiliar USB source or cable.
I erased my original post because I did not realize this was a purchasable product.
The headline implies that the cable was not suspect prior to the scan by calling it a USB cable and then following up with the sinister electronics label. In fact, they deliberately purchased a hackers tool and took a really cool scan of it. They were not surprised to find more than a standard USB cable. -
kuerious There are measures one can take:Reply
PortaPow USB-C Data Blocker (Twin Pack) https://a.co/d/1gxE0Tm
But if the die & antenna are capable of wireless connection, then these "USB digital condoms" are only so helpful. -
kep55 Reply
Am I missing something here? Why would a USB cable need any chips in it? Isn't the cable supposed to carry electrical signals from point A to point B?Admin said:Lumafield CT scanned the O.MG USB-C cable and discovered hidden advanced electronics with a sinister purpose.
O.MG USB-C cable CT scan reveals sinister active electronics — contains a hidden antenna and another die embedded in the microcontroller : Read more -
Reply
That's the entire point of the article. Such a cable shouldn't exist except as some sort of espionage device.kep55 said:Am I missing something here? Why would a USB cable need any chips in it? Isn't the cable supposed to carry electrical signals from point A to point B? -
purposelycryptic Reply
It's stated several times that this is a cable specifical designed for penetration testing by a security researcher. So, yes, it's a feature.JamesJones44 said:Did I miss read that the cable in question costs $119? If that's true, could this be a feature of the cable at that price vs malicious act?
The point of the article, and the company that scanned the cable, is that these kind of electronics can be surreptitiously built into cables for malicious purposes as well, and that a regular X-ray scan was not even able to detect the secondary IC. That makes them a potential threat in espionage and terrorist actions.
It's also one of the reasons why, at least when I was still working, computers in secure military and intelligence installations, as well as various corporate machines with access to restricted data, all had all their accessible USB ports physically disabled, and their IO devices permanently attached.
Securing against these sorts of threats has definitely become a lot harder over the past decade+, though. -
USAFRet Reply
Unless and until you xray it, you wouldn't know it was there.kep55 said:Am I missing something here? Why would a USB cable need any chips in it? Isn't the cable supposed to carry electrical signals from point A to point B?